Geo-location based policies – ranger – apache software foundation
Apache Ranger provides centralized to safeguard Enterprise Hadoop ecosystem, including fine-grained access control and centralized auditing. In .5 version, Apache Ranger introduced stack-model to really make it simpler for brand new components to make use of Apache Ranger authorization and auditing. Further, to allow extending/adapting Apache Ranger for brand new or deployment-specific authorization needs, the stack model provides hooks like context-enrichers and policy-conditions.
Within this document, we will have the facts of extending Apache Ranger to aid authorization in line with the location that the access is conducted i.e. country/condition/city that the resource is utilized.
This is actually the outline from the tasks to become done:
- Make a location computer file that contains Ip to location details mappings
- Register a context-enricher hook that contributes the place details towards the request
- Register an insurance policy-condition to ensure the client location matches the locations specified by the insurance policy
- Create/update Apache Ranger policies to specify the locations to permitOrrefuse the access
2 IP location computer file
IP location computer file is really a text file that contains comma separated fields. Each line within the file retain the location details for a variety of IP addresses. The format from the IP location computer file is offered below:
- Each line includes comma separated fields
- The very first lines are treated like a header, that contains names for every field
- Subsequent lines have location details for a variety of IP addresses
- First field may be the start IP-address from the range
- Second field may be the finish IP-address from the range
- Other fields possess the location data for that IP-range specified by first couple of fields (inclusive)
- IP-addresses ought to be specified as lengthy integers however the context-enricher can see addresses in us dot-notation when IPInDotFormat for that client IP-address true
- Example:
IP_FROM,IP_TO,COUNTRY_CODE,COUNTRY_NAME,REGION,CITY 10…255,10..3.,US,U . s . States,California,Santa Clara 20..100.80,20..100.89,US,U . s . States,Colorado,Broomfield 20..100.110,20..100.119,US,U . s . States,Texas,Irving
This data format is comparable to commercially accessible data from providers like IP2Location. Based upon the needs, the information file may either be sourced from the commercial data provider (like IP2Location) or perhaps be produced using the deployment specific details.
3 Register Context Enricher
When Apache Ranger wordpress plugin receives an authorization request, the request is undergone registered context-enrichers. The context enrichers get access to various request details – like user, resource utilized, access type, ip-address from the accessor, etc. The context enrichers can update the request context with a lot more information you can use while evaluating Ranger policies.
Context enricher RangerFileBasedGeolocationProvider, obtainable in tag-policy branch, adds geo-location data towards the request context, in line with the location details obtainable in an information file. To join up the context-enricher for any component (like HDFS/Hive/HBase/..), please update the component’s service-def by such as the following:
“contextEnrichers”: [ wordpress plugin.contextenricher.RangerFileBasedGeolocationProvider”, “enricherOptions”: ]
Please be sure that the computer file can be obtained towards the components in the location specified by the above mentioned registration (/etc/ranger/geo/geo.txt, within this example).
When RangerFileBasedGeolocationProvider receives an authorization request, it locates the record within the IP location data for that client Ip specified by the request. If your record is located, each field within the record will be included to the request context.
Following example will help comprehend the information on context data get added through the enricher:
- Client Ip: 20..100.85
- Matching record in IP location data:
- 20..100.80,20..100.89,”US”,”United States”,”Colorado”,”Broomfield”
- IP location data header:
- IP_FROM,IP_TO,COUNTRY_CODE,COUNTRY_NAME,REGION,CITY
- Records put into the request context:
- LOCATION_COUNTRY_CODE=US
- LOCATION_COUNTRY_NAME=U . s . States
- LOCATION_REGION=Colorado
- LOCATION_CITY=Broomfield
Please be aware that the context records would be the field name, prefixed with “LOCATION_”.
4 Register Policy Condition
Apache Ranger provides policy-condition hooks to complete custom conditions while evaluating authorization demands. To look for the authorization result, Apache Ranger policy engine evaluates the policies which are relevant towards the utilized resource. Only if various criteria like user/group, access-type and policy-conditions specified by the insurance policy matches the request, the insurance policy engine uses the insurance policy to look for the result.
Policy condition RangerContextAttributeValueNotInCondition, obtainable in tag-policy branch, returns true only if the required request context value doesn’t match the specified by the insurance policy. This can be to see if the place in request context (that is populated through the context enricher detailed earlier) is outdoors the specified by the insurance policy – for instance, to deny use of demands that originate outdoors of specified countries. To join up the insurance policy-condition for any component (like HDFS/Hive/HBase/..), please update the component’s service-def by such as the following:
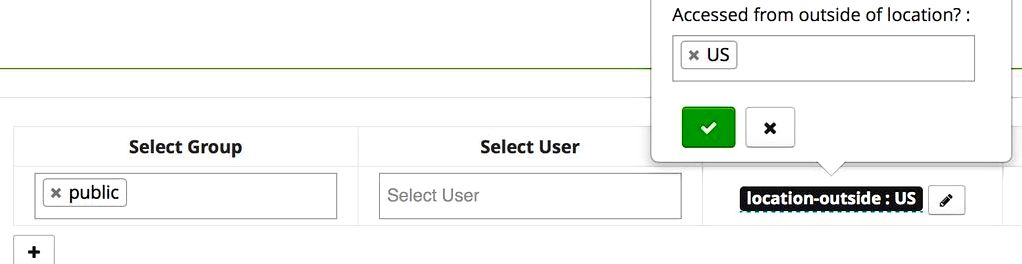
“policyConditions”: [ outdoors”, “label”: “Utilized from outdoors of location?”, “description”: “Utilized from outdoors of location?”, “evaluator”: “org.apache.ranger.wordpress plugin.conditionevaluator.RangerContextAttributeValueNotInCondition”, “evaluatorOptions”: ]Once this insurance policy condition is registered with Ranger, the insurance policy editing UI will prompt for condition values for use during evaluation – as proven below
Apache Ranger provides centralized to safeguard Enterprise Hadoop ecosystem, including fine-grained access control and centralized auditing. In .5 version, Apache Ranger introduced stack-model to really make it simpler for brand new components to make use of Apache Ranger authorization and auditing. Further, to allow extending/adapting Apache Ranger for brand new or deployment-specific authorization needs, the stack model provides hooks like context-enrichers and policy-conditions.
Within this document, we will have the facts of extending Apache Ranger to aid authorization in line with the location that the access is conducted i.e. country/condition/city that the resource is utilized.
This is actually the outline from the tasks to become done:
- Make a location computer file that contains Ip to location details mappings
- Register a context-enricher hook that contributes the place details towards the request
- Register an insurance policy-condition to ensure the client location matches the locations specified by the insurance policy
- Create/update Apache Ranger policies to specify the locations to permitOrrefuse the access
2 IP location computer file
IP location computer file is really a text file that contains comma separated fields. Each line within the file retain the location details for a variety of IP addresses. The format from the IP location computer file is offered below:
- Each line includes comma separated fields
- The very first lines are treated like a header, that contains names for every field
- Subsequent lines have location details for a variety of IP addresses
- First field may be the start IP-address from the range
- Second field may be the finish IP-address from the range
- Other fields possess the location data for that IP-range specified by first couple of fields (inclusive)
- IP-addresses ought to be specified as lengthy integers however the context-enricher can see addresses in us dot-notation when IPInDotFormat for that client IP-address true
- Example:
IP_FROM,IP_TO,COUNTRY_CODE,COUNTRY_NAME,REGION,CITY 10…255,10..3.,US,U . s . States,California,Santa Clara 20..100.80,20..100.89,US,U . s . States,Colorado,Broomfield 20..100.110,20..100.119,US,U . s . States,Texas,Irving
This data format is comparable to commercially accessible data from providers like IP2Location. Based upon the needs, the information file may either be sourced from the commercial data provider (like IP2Location) or perhaps be produced using the deployment specific details.
3 Register Context Enricher
When Apache Ranger wordpress plugin receives an authorization request, the request is undergone registered context-enrichers. The context enrichers get access to various request details – like user, resource utilized, access type, ip-address from the accessor, etc. The context enrichers can update the request context with a lot more information you can use while evaluating Ranger policies.
Context enricher RangerFileBasedGeolocationProvider, obtainable in tag-policy branch, adds geo-location data towards the request context, in line with the location details obtainable in an information file. To join up the context-enricher for any component (like HDFS/Hive/HBase/..), please update the component’s service-def by such as the following:
“contextEnrichers”: [ wordpress plugin.contextenricher.RangerFileBasedGeolocationProvider”, “enricherOptions”: ]
Please be sure that the computer file can be obtained towards the components in the location specified by the above mentioned registration (/etc/ranger/geo/geo.txt, within this example).
When RangerFileBasedGeolocationProvider receives an authorization request, it locates the record within the IP location data for that client Ip specified by the request. If your record is located, each field within the record will be included to the request context.
Following example will help comprehend the information on context data get added through the enricher:
- Client Ip: 20..100.85
- Matching record in IP location data:
- 20..100.80,20..100.89,”US”,”United States”,”Colorado”,”Broomfield”
- IP location data header:
- IP_FROM,IP_TO,COUNTRY_CODE,COUNTRY_NAME,REGION,CITY
- Records put into the request context:
- LOCATION_COUNTRY_CODE=US
- LOCATION_COUNTRY_NAME=U . s . States
- LOCATION_REGION=Colorado
- LOCATION_CITY=Broomfield
Please be aware that the context records would be the field name, prefixed with “LOCATION_”.
4 Register Policy Condition
Apache Ranger provides policy-condition hooks to complete custom conditions while evaluating authorization demands. To look for the authorization result, Apache Ranger policy engine evaluates the policies which are relevant towards the utilized resource. Only if various criteria like user/group, access-type and policy-conditions specified by the insurance policy matches the request, the insurance policy engine uses the insurance policy to look for the result.
Policy condition RangerContextAttributeValueNotInCondition, obtainable in tag-policy branch, returns true only if the required request context value doesn’t match the specified by the insurance policy. This can be to see if the place in request context (that is populated through the context enricher detailed earlier) is outdoors the specified by the insurance policy – for instance, to deny use of demands that originate outdoors of specified countries. To join up the insurance policy-condition for any component (like HDFS/Hive/HBase/..), please update the component’s service-def by such as the following:
“policyConditions”: [ outdoors”, “label”: “Utilized from outdoors of location?”, “description”: “Utilized from outdoors of location?”, “evaluator”: “org.apache.ranger.wordpress plugin.conditionevaluator.RangerContextAttributeValueNotInCondition”, “evaluatorOptions”: ]Once this insurance policy condition is registered with Ranger, the insurance policy editing UI will prompt for condition values for use during evaluation – as proven below:
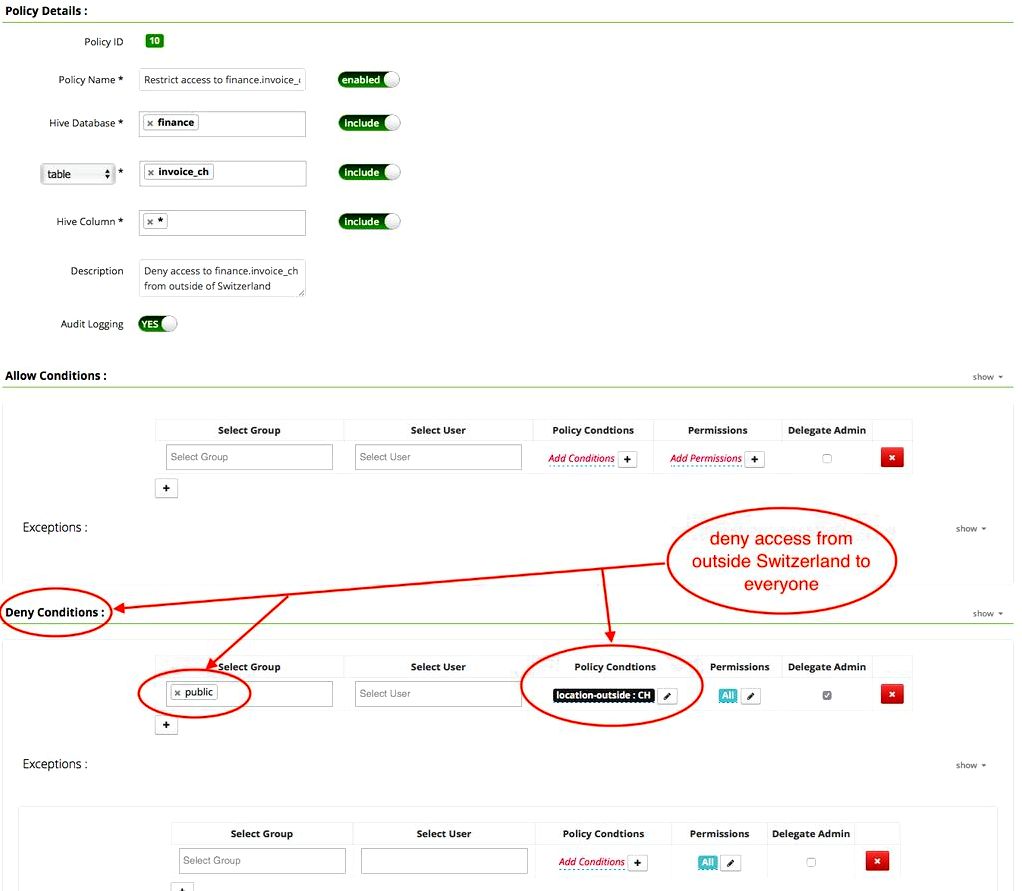
5 Example: Deny use of a Hive table from outdoors a particular country
Within this section, we will have the facts of the Apache Ranger policy that denies use of a particular Hive table when utilized from the location outdoors of the specific country. This situation uses the context-enricher and policy-condition described earlier within this document.
Resourse: https://cwiki.apache.org/confluence/display/RANGER/