What’s ipsec (ip address security)? – definition from whatis.com
Contents
- IPsec protocols
- How IPsec works
- IPsec protocols
- How IPsec works
- IPsec Virtual private network and IPsec modes
- ipsec overview
IPsec initially defined two mechanisms for imposing security on IP packets: the Encapsulating Security Payload (ESP) protocol, which defined a technique for encrypting data in IP packets, and also the Authentication Header (AH) protocol, which defined a technique for digitally signing IP packets. The Web Key Exchange (IKE) protocol can be used to handle the cryptographic keys utilized by hosts for IPsec.
IPsec may be used to safeguard network data, for instance, by establishing circuits using IPsec tunneling, by which all data being sent between two endpoints is encrypted, just like an online Private Network (Virtual private network) connection for encrypting application layer data as well as for supplying to safeguard routers delivering routing data over the public internet. IPsec may also be used to supply authentication without file encryption, for instance to authenticate that data arises from a known sender.
Internet traffic could be guaranteed from location of host without using IPsec, for instance by file encryption in the application layer (Layer 7 from the OSI model) with HTTP Secure (HTTPS) or in the transport layer (Layer 4 from the OSI model) using the Transport Layer Security (TLS) protocol. However, when traffic uses file encryption or authentication at these greater layers, threat actors can always have the ability to intercept protocol information which may expose data that needs to be encrypted.
IPsec protocols
IPsec is determined to be used with current versions from the Ip Address, IPv4 and IPv6. IPsec protocol headers are incorporated within the IP header, where they seem as IP header extensions whenever a product is using IPsec.
The most crucial protocols considered part of IPsec include:
- The IP Authentication Header (AH), specified by RFC 4302, defines an optional packet header for use to ensure connectionless integrity and knowledge origin authentication for IP packets, and also to safeguard against replays.
- The IP Encapsulating Security Payload (ESP), specified by RFC 4303, defines an optional packet header you can use to supply confidentiality through file encryption from the packet, in addition to integrity protection, data origin authentication, access control and optional protection against replays or traffic analysis.
- Internet Key Exchange (IKE), defined in RFC 7296, “Internet Key Exchange Protocol Version 5 (IKEv2),” is really a protocol defined to permit hosts to specify which services should be incorporated in packets, which cryptographic algorithms will be employed to provide individuals services, along with a mechanism for discussing the keys combined with individuals cryptographic algorithms.
- Formerly defined by itself, the web Security Association and Key Management Protocol (ISAKMP) has become specified included in the IKE protocol specs. ISAKMP defines how Security Associations (SAs) are positioned up and accustomed to define direct connections between two hosts which are using IPsec. Each SA defines an association, one way, in one location of another a set of hosts could be based on two SAs. The SA includes all relevant features of the bond, such as the cryptographic formula getting used, the IPsec mode getting used, file encryption key and then any other parameters associated with the transmission of information within the connection.
Numerous other protocols and algorithms use or are utilized by IPsec, including file encryption and digital signature algorithms, and many related protocols are described in RFC 6071, “IP Security (IPsec) and Internet Key Exchange (IKE) Document Roadmap.”
How IPsec works
The initial step while using IPsec takes place when a number sees that a packet ought to be transmitted using IPsec. This can be made by examining the Ip from the source or destination against policy configurations to find out if the traffic should be thought about “interesting” for IPsec purposes. Interesting traffic triggers the safety insurance policy for the packets, meaning the machine delivering the packet applies the right file encryption and/or authentication towards the packet. When an incoming packet is decided to become “interesting,” the host verifies the inbound packet continues to be encrypted and/or authenticated correctly.
The 2nd part of the IPsec process, known as IKE Phase 1, enables the 2 hosts using IPsec to barter the insurance policy sets they will use for that guaranteed circuit, authenticate themselves to one another, and initiate a safe and secure funnel backward and forward hosts.
IKE Phase 1 creates a preliminary secure funnel between hosts using IPsec that secure funnel will be accustomed to safely negotiate how a IPsec circuit will secure and/or authenticate data sent over the IPsec circuit.
IPsec initially defined two mechanisms for imposing security on IP packets: the Encapsulating Security Payload (ESP) protocol, which defined a technique for encrypting data in IP packets, and also the Authentication Header (AH) protocol, which defined a technique for digitally signing IP packets. The Web Key Exchange (IKE) protocol can be used to handle the cryptographic keys utilized by hosts for IPsec.
IPsec may be used to safeguard network data, for instance, by establishing circuits using IPsec tunneling, by which all data being sent between two endpoints is encrypted, just like an online Private Network (Virtual private network) connection for encrypting application layer data as well as for supplying to safeguard routers delivering routing data over the public internet. IPsec may also be used to supply authentication without file encryption, for instance to authenticate that data arises from a known sender.
Internet traffic could be guaranteed from location of host without using IPsec, for instance by file encryption in the application layer (Layer 7 from the OSI model) with HTTP Secure (HTTPS) or in the transport layer (Layer 4 from the OSI model) using the Transport Layer Security (TLS) protocol. However, when traffic uses file encryption or authentication at these greater layers, threat actors can always have the ability to intercept protocol information which may expose data that needs to be encrypted.
IPsec protocols
IPsec is determined to be used with current versions from the Ip Address, IPv4 and IPv6. IPsec protocol headers are incorporated within the IP header, where they seem as IP header extensions whenever a product is using IPsec.
The most crucial protocols considered part of IPsec include:
- The IP Authentication Header (AH), specified by RFC 4302, defines an optional packet header for use to ensure connectionless integrity and knowledge origin authentication for IP packets, and also to safeguard against replays.
- The IP Encapsulating Security Payload (ESP), specified by RFC 4303, defines an optional packet header you can use to supply confidentiality through file encryption from the packet, in addition to integrity protection, data origin authentication, access control and optional protection against replays or traffic analysis.
- Internet Key Exchange (IKE), defined in RFC 7296, “Internet Key Exchange Protocol Version 5 (IKEv2),” is really a protocol defined to permit hosts to specify which services should be incorporated in packets, which cryptographic algorithms will be employed to provide individuals services, along with a mechanism for discussing the keys combined with individuals cryptographic algorithms.
- Formerly defined by itself, the web Security Association and Key Management Protocol (ISAKMP) has become specified included in the IKE protocol specs. ISAKMP defines how Security Associations (SAs) are positioned up and accustomed to define direct connections between two hosts which are using IPsec. Each SA defines an association, one way, in one location of another a set of hosts could be based on two SAs. The SA includes all relevant features of the bond, such as the cryptographic formula getting used, the IPsec mode getting used, file encryption key and then any other parameters associated with the transmission of information within the connection.
Numerous other protocols and algorithms use or are utilized by IPsec, including file encryption and digital signature algorithms, and many related protocols are described in RFC 6071, “IP Security (IPsec) and Internet Key Exchange (IKE) Document Roadmap.”
How IPsec works
The initial step while using IPsec takes place when a number sees that a packet ought to be transmitted using IPsec. This can be made by examining the Ip from the source or destination against policy configurations to find out if the traffic should be thought about “interesting” for IPsec purposes. Interesting traffic triggers the safety insurance policy for the packets, meaning the machine delivering the packet applies the right file encryption and/or authentication towards the packet. When an incoming packet is decided to become “interesting,” the host verifies the inbound packet continues to be encrypted and/or authenticated correctly.
The 2nd part of the IPsec process, known as IKE Phase 1, enables the 2 hosts using IPsec to barter the insurance policy sets they will use for that guaranteed circuit, authenticate themselves to one another, and initiate a safe and secure funnel backward and forward hosts.
IKE Phase 1 creates a preliminary secure funnel between hosts using IPsec that secure funnel will be accustomed to safely negotiate how a IPsec circuit will secure and/or authenticate data sent over the IPsec circuit.
There’s two options during IKE Phase 1: Primary mode or Aggressive mode. Primary mode provides greater security since it creates a safe and secure tunnel for exchanging session algorithms and keys, while Aggressive mode enables a few of the session configuration data to become passed as plaintext but enables hosts to determine an IPsec circuit more rapidly.
Under Primary mode, the host initiating the session transmits a number of proposals for that session, indicating the file encryption and authentication algorithms it would rather use, along with other facets of the bond the responding host continues the settlement before the two hosts agree and establish an IKE Security Association (SA), which defines the IPsec circuit.
When Aggressive mode is being used, the host initiating the circuit specifies the IKE security association data unilaterally as well as in the obvious, using the responding host responding by authenticating the session.
The 3rd part of establishing an IPsec circuit may be the IKE Phase 2, which is conducted within the secure funnel setup in IKE Phase 1. It takes the 2 hosts to barter and initiate the safety association for that IPsec circuit transporting actual network data. Within the second phase, the 2 hosts negotiate the kind of cryptographic algorithms to make use of around the session, in addition to saying yes on secret keying material for use with individuals algorithms. Nonces, at random selected figures used just once to supply session authentication and replay protection, are exchanged within this phase. The hosts might also negotiate to enforce perfect forward secrecy around the exchange within this phase.
Fourth step from the IPsec connection may be the actual exchange of information over the recently produced IPsec encrypted tunnel. From here, packets are encrypted and decrypted through the two endpoints while using IPsec SAs setup in the last three steps.
The final step is termination from the IPsec tunnel, usually once the communication between your hosts is finished, once the session occasions out or whenever a formerly specified quantity of bytes continues to be undergone the IPsec tunnel. Once the IPsec tunnel is ended, the hosts discard keys used over that security association.
IPsec Virtual private network and IPsec modes
IPsec protocols may be used to assemble a Virtual private network connection, to secure and/or authenticate all traffic between several points. IPsec circuits, including VPNs, could be established to use two modes:
Tunnel mode: Usually used between guaranteed network gateways, IPsec tunnel mode enables hosts behind among the gateways to speak safely with hosts behind another gateway. For instance, any users of systems within an enterprise branch office can safely interact with any systems within the primary office when the branch office and primary office have secure gateways to do something as IPsec proxies for hosts inside the particular offices. The IPsec tunnel is made backward and forward gateway hosts, however the tunnel itself can transport traffic from the hosts within the protected systems. Tunnel mode is helpful for establishing a mechanism for safeguarding all traffic between two systems, from disparate hosts on either finish.
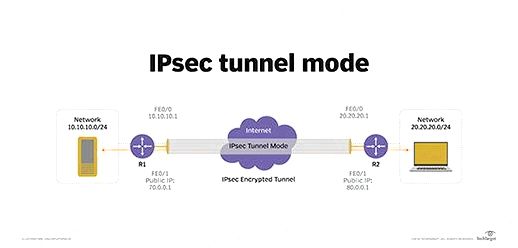
IPsec enables an encrypted tunnel over the public internet for securing LAN packets sent between remote locations.
Resourse: https://searchsecurity.techtarget.com/definition/