Security ip suite
iWave offers Services and IP for secure OS / IoT:

- Secure Boot
- Secure OS – TrustZone Technology
- OPTEE OS Porting
- OPTEE Driver Development: PINPAD, GPIO, I2C, SPI, LCDIF
- Reliable Application (TA), PTA and OPTEE-Client: Development and Porting
- Image Authentication and Verification (Cryptography)
- Tamper Recognition & Data Protection
-
Secure Transaction (IoT and Payment)
Why Security is essential ….??!
The immense have to address this peace of mind in Embedded Systems, invades following protection of information:
- Personal Information: If security is compromised, finish user is impacted directly. For instance, in situation of online banking passwords.
-
Restricted Data: If security is compromised, the information provider is impacted heavily. For instance, digital multimedia content for example copyrighted digital photos, video and audio contents.
In connected devices, this secure information is transferred through public systems. So, you should make sure that secure data is protected against unauthorized access thus making certain security.
Peace of mind in Embedded System:
Peace of mind in Embedded Product is mostly mixture of Hardware, Software and Mechanical solutions. Hardware option would be like Secure SoC, Secure ROM, TrustZone, Hardware Cryptography, Tamper Recognition etc. Software solution includes software file encryption algorithms, Reliable Software. In the majority of the cases it will likely be a mix of Software and hardware means to fix ensure greatest security.
Tamper Recognition:
Tamper Recognition module will give you the physical protection for that devices. In situation associated with a tampering, the Tamper recognition modules informs the SoC from the corresponding occasions as below
- Exterior Tamper
- Exterior PIN
- Internal Tamper
- Current
- Temperature
-
Clock
Once the SoC detects the tampering event, a burglar breach alarm is asserted for
- Software Action
- Security hardware contained in SoC will the following
- Will deny use of the modules (bandwith)


-
iWave offers Services and IP for secure OS / IoT:

- Secure Boot
- Secure OS – TrustZone Technology
- OPTEE OS Porting
- OPTEE Driver Development: PINPAD, GPIO, I2C, SPI, LCDIF
- Reliable Application (TA), PTA and OPTEE-Client: Development and Porting
- Image Authentication and Verification (Cryptography)
- Tamper Recognition & Data Protection
-
Secure Transaction (IoT and Payment)
Why Security is essential ….??!
The immense have to address this peace of mind in Embedded Systems, invades following protection of information:
- Personal Information: If security is compromised, finish user is impacted directly. For instance, in situation of online banking passwords.
-
Restricted Data: If security is compromised, the information provider is impacted heavily. For instance, digital multimedia content for example copyrighted digital photos, video and audio contents.
In connected devices, this secure information is transferred through public systems. So, you should make sure that secure data is protected against unauthorized access thus making certain security.
Peace of mind in Embedded System:
Peace of mind in Embedded Product is mostly mixture of Hardware, Software and Mechanical solutions. Hardware option would be like Secure SoC, Secure ROM, TrustZone, Hardware Cryptography, Tamper Recognition etc. Software solution includes software file encryption algorithms, Reliable Software. In the majority of the cases it will likely be a mix of Software and hardware means to fix ensure greatest security.
Tamper Recognition:
Tamper Recognition module will give you the physical protection for that devices. In situation associated with a tampering, the Tamper recognition modules informs the SoC from the corresponding occasions as below
- Exterior Tamper
- Exterior PIN
- Internal Tamper
- Current
- Temperature
-
Clock
Once the SoC detects the tampering event, a burglar breach alarm is asserted for
- Software Action
- Security hardware contained in SoC will the following
- Will deny use of the modules (bandwith)


-
All secure memory contents (Eg: Guaranteed Keys) kept in the interior RAM is going to be erased

Secure Boot:
Many SOC manufacturers provide “Secure Boot” option which adds cryptographic checks to every stage from the Secure boot process. The firmware code is signed while using device manufacturer’s code verification private key. The Secure Bootloader, on boot up checks the validity from the code by verifying the signature while using code verification public-key.
Cryptographic signature algorithms:
Cryptographic algorithms are utilized to secure and decrypt the information. Including used Cryptographic algorithms are public key- private key cryptographic algorithms. This formula uses two different but in past statistics linked keys.
- Before delivering with other device, Private secret is accustomed to secure the information and create the encrypted data.
-
Public secret is distributed to everybody. Understanding formula makes use of this public answer to decrypt the encrypted data and acquire the initial data.


Similar Cryptographic algorithms approach can be used in secure boot with couple of enhancements. Here together with cryptographic algorithms, certain measures are taken so the system can’t be hacked.
In Secure Boot, Public secret is encrypted and kept in one-time programmable registers.
ROM code includes a signature verification module and also the code verification public-answer to verify the firmware code.
- Generate private key and public key using device manufacturer’s code.
- The look is signed using the device manufacturer’s private key using signature formula. This signed image is developed to hard drive.
- Public secret is encrypted and burned to fuses.
- The ROM code, on boot up checks the validity from the signed image by verifying the signature while using public-key.
-
If signature applies, then image will boot. Otherwise board will fail as well.
Why it’s Secure…!!!

- ROM code resides inside a write protected ROM. This helps to ensure that the Secure Boot loader is never modified.
- The non-public secret is always stored secret through the device manufacturer. Public key needs to be stored inside the device inside a manner, in order that it can’t be substituted with an open key owed for an attacker. This is accomplished by writing public answer to one-time programmable registers.
-
Public secret is also encrypted before conntacting one-time programmable registers. This helps to ensure that only device manufacturer’s “signature verification code” can decrypt it and employ it to ensure the signed image.
Chain of Trust:

A safe and secure boot checks for “authenticated image” in each and every stage of boot process. This method aims to determine the integrity from the “authenticated image”, hence stopping any unauthorized software from running.
The secure boots depends on the thought of “Chain of Trust”. Beginning by having an unconditionally reliable component, almost every other component could be authenticated prior to being performed, hence always only authenticated reliable image is running.
- ROM code verifies & authenticates the signed first stage boot loader.
- The first stage boot loader verifies & authenticates the signed second stage boot loader.
-
The second stage boot loader verifies & authenticates the signed OS image adopted by file system mounting and launching the applying.
ARM TrustZone:
Arm TrustZone technologies are a method on Nick (SoC) and CPU system-wide method for security. TrustZone is hardware-based security included in SoCs by semiconductor nick designers who wish to provide secure finish points along with a device cause of trust.
Reliable OS like OPTEE (Open Portable Reliable Execution Atmosphere) runs safely on Trustzone hardware baked into the SoC. The processor core of SoC has two virtual cores: Secure and Non-Secure
- Secure world runs Reliable OS like OP-TEE – ARM Reliable Zone
-
Non-Secure world runs Wealthy OS like Linux (REE) – ARM Cortex A
The Secure Boot loader (ROM) within the SoC helps to ensure that the unit boots track of the Secure OS/firmware with right process rights. The Memory Management Unit (MMU) configured through the OS permits the accessibility buffers within the Internal RAM which involves secret key operations simply to the secure processes with special OS rights.
OP-TEE OS running in TrustZone provides key features like isolation from REE, small footprint and portability.
For more information details about OPTEE OS refer: http://www.iwavesystems.com/situation-studies/software-design-services/optee-imx6ul-secure-connectivity-solution.html

Secure IoT:
IoT Communication using the cloud over MQTT is guaranteed with SSL/TLS. Every bandwith is going to be encrypted using TLS protocol. Aside from SSL/TLS, Cloud might have its very own authentication methods and policies to permitOrlimit the bond.
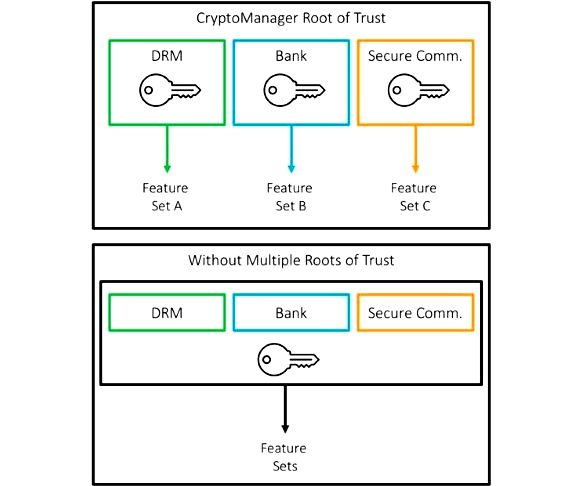
Resourse: https://iwavesystems.com/engineering-services/software-design-services/
Security Official Trailer #1 (2017) Antonio Banderas Action Movie HD
