An operating help guide to nmap (network security scanner) in kali linux
Within the second Kali Linux article, the network tool referred to as ‘nmap‘ is going to be discussed. While nmap isn’t a Kali only tool, it is among the most helpful network mapping tools in Kali.
- Kali Linux Installation Guide for novices – Part 1
Nmap, short for Network Mapper, is maintained by Gordon Lyon (much more about Mr. Lyon here: http://insecure.org/fyodor/) and it is used by lots of security professionals around the globe.
Within the second Kali Linux article, the network tool referred to as ‘nmap‘ is going to be discussed. While nmap isn’t a Kali only tool, it is among the most helpful network mapping tools in Kali.
- Kali Linux Installation Guide for novices – Part 1
Nmap, short for Network Mapper, is maintained by Gordon Lyon (much more about Mr. Lyon here: http://insecure.org/fyodor/) and it is used by lots of security professionals around the globe.
The utility works both in Linux and Home windows and it is command line (CLI) driven. But also for individuals a bit more timid from the command line, there’s an excellent graphical frontend for nmap known as zenmap.
It’s strongly suggested that folks discover the CLI form of nmap because it provides a lot more versatility in comparison to the zenmap graphical edition.
What purpose does nmap server? Great question. Nmap enables to have an administrator to rapidly and completely find out about the systems on the network, and so the name, Network MAPper or nmap.
Nmap is able to rapidly locate live hosts in addition to services connected with this host. Nmap’s functionality could be extended even more using the Nmap Scripting Engine, frequently abbreviated as NSE.
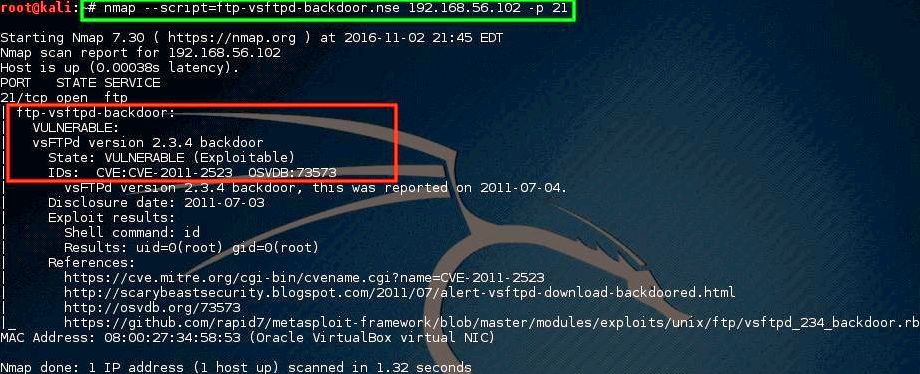
This scripting engine enables managers to rapidly produce a script you can use to find out if your recently discovered vulnerability exists on their own network. Many scripts happen to be developed and incorporated with many nmap installs.
A thing of caution – nmap is really a generally utilized by individuals with both negative and positive intentions. Extreme care ought to be taken to actually aren’t using nmap against systems that permission hasn’t be clearly provided inside a written/legal agreement. Please be careful while using the nmap tool.
System Needs
- Kali Linux (nmap will come in other os’s and processes such as this guide).
- Another computer and permission to scan that computer with nmap – This really is frequently easily completed with software for example VirtualBox and the development of an online machine.
- For any good machine to rehearse with, please find out about Metasploitable 2
- Download for MS2 Metasploitable2
- A legitimate working link with a network or maybe using virtual machines, a legitimate internal network connection for that two machines.
Kali Linux – Dealing with Nmap
The initial step to dealing with nmap would be to sign in to the Kali Linux machine and when preferred, begin a graphical session (This primary article within this series installed Kali Linux using the Enlightenment Desktop Atmosphere).
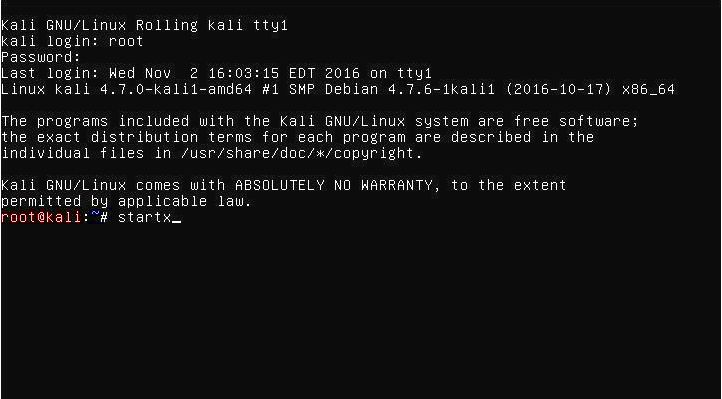
Throughout the installation, the installer might have motivated the consumer for any ‘root‘ user password which is required to login. Once logged to the Kali Linux machine, while using command ‘startx‘ the Enlightenment Desktop Atmosphere could be began – it’s important to note that nmap doesn’t need a desktop atmosphere to operate.
# startx
Resourse: https://tecmint.com/nmap-network-security-scanner-in-kali-linux/
